Tune KVM Hypervisor with directly attached MacVTap driver to VLAN device or with bridge to VLAN device
I have working during many years with VmWare (read for example my articles from 2019 year VmWare 7 management or from 2010 year Основы работы с VmWare, but this project I decide to making with KVM Hypervisor because there are a couple of benefits of this solution:
- a lot of server does not support VmWare at all
- avoid to receive license from VmWare
- cheapest datacenter in the world https://www.hetzner.com/ support installation KVM hypervisor by one mouse click and not support VmWare at all
- simplify protection of hypervisor
1. Install KVM.
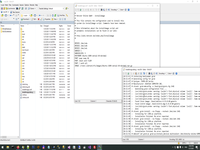
# apt-get update # apt-get upgrade # apt-get install qemu-kvm libvirt-bin virtinst bridge-utils cpu-checker libvirt-daemon-system # kvm-ok # service libvirtd status
2. Protect KVM hypervisor by UFW.
So, first step is protection. Simplest protection is only restriction to server from one address.
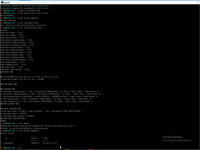
But in practice need more complex and sophisticated rules. To reorder UFW rules need to change order in /etc/default/ufw. In this case only server admin has access to KVM hypervisor. If server admin IP addr is changing need to require console access from datacenter.
# apt install ufw # ufw allow from XXX.XXX.XXX.XXX to any port 22 # ufw enable # ufw status numbered
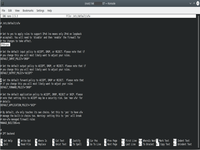
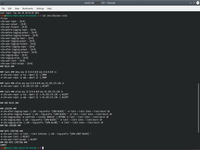
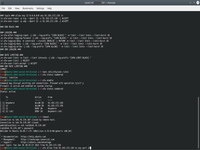
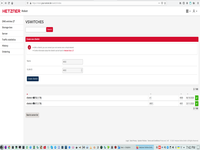
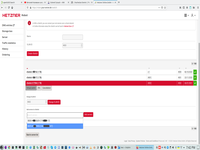
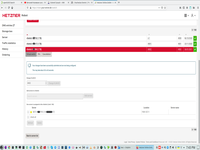
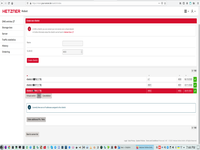
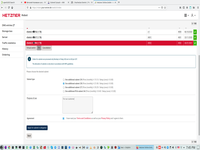
3. Define virtual switch with VLAN and receive IP addr for that switch.
4. Install VLAN kernel support.
# sudo sh -c 'grep -q 8021q /etc/modules || echo 8021q >> /etc/modules' # modprobe 8021q
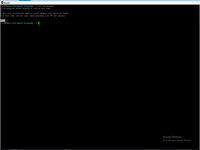
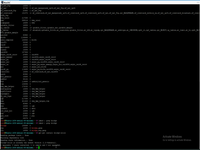
Relogin or restart the kernel modules
# rmmod kvm # modprobe -a kvm
5. Define server interface for that VLAN.
# apt-get install vlan # sudo nano /etc/network/interfaces # reboot
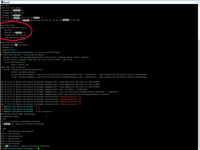
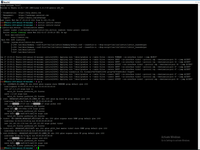
And check how it working.
# cat /proc/net/vlan/eth0.4002
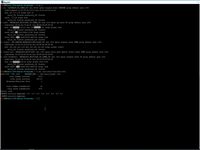
6. Select MacVTap driver for VLAN device as external interface of VM.
This is cool and important point, if VM will be working in this point than all going well.
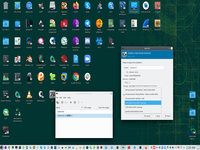
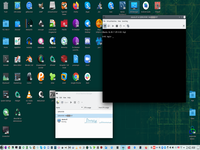
But, unfortunately, this is not all. Because we have no bridge, therefore only one VM will be working in KVM.
7. Define bridge.
In final step I define in my KVM host a bridge over my physical interface with VLAN. This allow me connect to bridge more than one VM (as in previous step)
# sudo nano /etc/network/interfaces
auto br1
iface br1 inet static
mtu 1400
address xxx.xxx.xxx.xxx
netmask 255.255.255.240
bridge_ports eth0.4002
bridge_stp off
bridge_fd 0
bridge_maxwait 0
metric 1
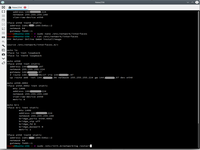
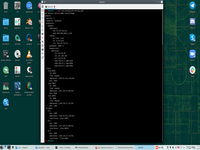
After that any VM can connect to bridge.
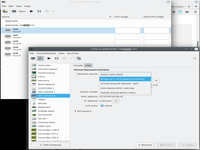
And enjoy.
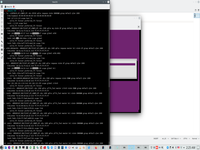
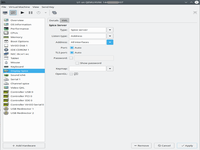
8. Permission to spice server.
In this configuration need to set special permission to spice server.
Without this permission you will receive only error.
Of course, you can download spice client for windows and with this permission it will be also working well.
More:
- Of course, you can make all of this operation from command line. This is good doc of virsh commands.
- virt-manager
Kvm context:
 )
)
|
|