How to create SSL endpoint to NGINX reverse proxy with Basic AU
This is very spread task and this workflow I repeat in many servers with little differences.
A couple times I made a same mistake, so I decide to describe this task step-by-step. Firstly, need to buy SSL certificate. A couple times I use https://cheapsslsecurity.com/. Main future of this site that it can not store private key and after a time you will receive SSL certificate without private key. So, if you don't store private key, you certificate is uselessness.
Most important step is check accordance between CRT and PrivateKey. This to command show MD5 sign. Hash must be equal.
# openssl rsa -noout -modulus -in "G:\Projects\Certificates\CryptochestCert-Docker\docker001.cryptochest.io.key"| openssl md5 # openssl x509 -noout -modulus -in "G:\Projects\Certificates\CryptochestCert-Docker\CER - CRT Files\docker001_cryptochest_io.crt"| openssl md5
One of the huge mistake is installing to windows wrong compiled version of SSL. I'm faced with this issue a couple of times. Correct version of SSL need to take from GIT folder.
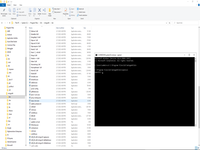
So, this Private Key is correct to this Certificate.
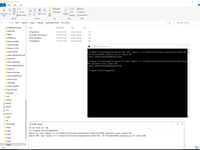
Next important operation is combine certificate with root to bundle. Main mistake in this step is order to create bundle certificate.
# cat cert/docker001_cryptochest_io.crt cert/My_CA_Bundle.crt > cert/docker001-bundle.crt
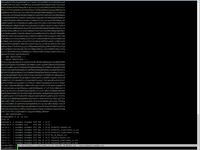
And than, of course, need to copy certificates to right directory. In my case:
# sudo cp cert/docker001-bundle.crt /etc/ssl/certs/docker001-bundle.crt # sudo cp cert/docker001.cryptochest.io.key /etc/ssl/private/docker001.cryptochest.io.key
Next step is creating .htaccess file to store login/password with Basic AU.
# sudo sh -c "echo -n 'docker:' > /etc/nginx/.htpasswd" # sudo sh -c "openssl passwd -apr1 >> /etc/nginx/.htpasswd" # cat /etc/nginx/.htpasswd
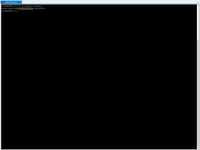
Next step is create correct config, in my case with reverse proxy config looks as:
# cat /etc/nginx/sites-available/docker
upstream docker {
server unix:/var/run/docker.sock;
}
server {
listen 4444 default_server ssl;
server_name docker001.cryptochest.io;
ssl on;
ssl_certificate /etc/ssl/certs/docker001-bundle.crt;
ssl_certificate_key /etc/ssl/private/docker001.cryptochest.io.key;
location / {
proxy_pass http://docker;
auth_basic_user_file /etc/nginx/.htpasswd;
auth_basic "Access restricted";
}
}
But this is not all. For docker need to change Nginx account (nginx User directives and close port 80, opened by default). This operation need to do in main Nginx config file.
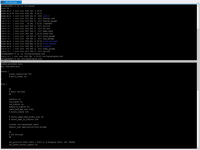
Cool, all preparation is done. Now time to check what we done.
# sudo ln -s /etc/nginx/sites-available/docker /etc/nginx/sites-enabled/ # sudo service nginx restart # systemctl status nginx.service
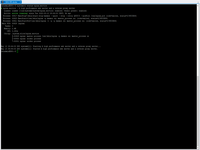
Pay attention to firewall and listened port.
# sudo netstat -tunlp # netstat -atun # sudo ufw status
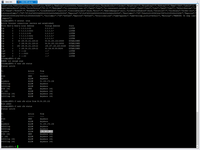
All job done and now I try to complex check all my certificates, Basic AU with my password, my Nginx reverse proxy and my docker behind proxy.
# curl -X GET --user "docker:XXXXXXXXXXXXX" -i "https://docker001.cryptochest.io:4444/info"

And final complex test is test of my firewall.
Cool, current job is done. And as bonus you can see a Nginx config for protection Docker Registry with the same way docker-registry.txt
DevEnvironment context:
Servers context:
Ssl context:
 )
)
|
|