Close unauthorized access to Confluent Control Center by WireGuard
1. Install Confluent Control Center.
There are instruction about installation KAFKA message broker with connectors and related services https://docs.confluent.io/platform/current/installation/installing_cp/zip-tar.html, And instruction little bit wrong, first step need to install JAVA.
# sudo apt update # sudo apt install default-jre # java -version
And maybe JDK.
# sudo apt install default-jdk # javac -version
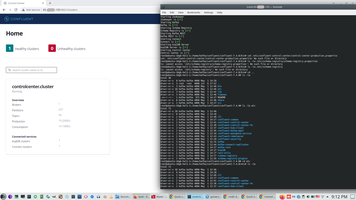
In my case this is home of installation.
# export CONFLUENT_HOME=/home/kafka/confluent/confluent-7.4.0
Unfortunately after installation service allow with external IP for anybody. This page describe solution to avoid unauthorized access.
2. Install WireGuard server.
The simplest way to close access is using my liked VPN https://www.wireguard.com/install/ and this solution allow many other benefits.
# sudo apt update # sudo apt install wireguard
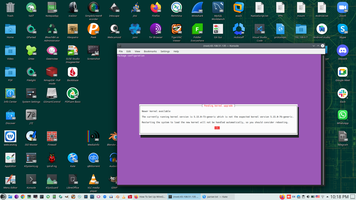
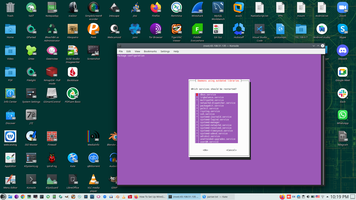
In my case Kernel update needed firstly.
2.1. Generate pair of Private/Public key.
# wg genkey | sudo tee /etc/wireguard/private.key # sudo chmod go= /etc/wireguard/private.key # sudo cat /etc/wireguard/private.key | wg pubkey | sudo tee /etc/wireguard/public.key
Next need to select IPv4 address for VPN from private IP4 Range. IPv6 - we can select any random varue with prefix FD, you can combine for example time and unique machine id /var/lib/dbus/machine-id.
- 10.0.0.0 to 10.255.255.255 (10/8 prefix)
- 172.16.0.0 to 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 to 192.168.255.255 (192.168/16 prefix)
2.2. Setup WireGuard config.
And add selected IP range to WireGuard config.
# sudo nano /etc/wireguard/wg0.conf
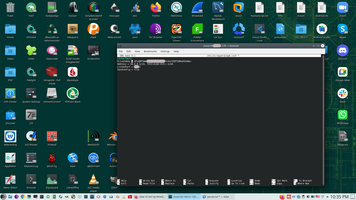
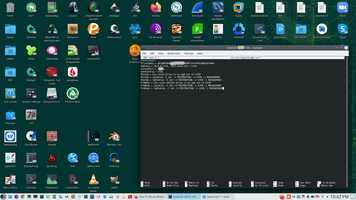
Magic string on the and of config
PostUp = ufw route allow in on wg0 out on eth0 PostUp = iptables -t nat -I POSTROUTING -o eth0 -j MASQUERADE PostUp = ip6tables -t nat -I POSTROUTING -o eth0 -j MASQUERADE PreDown = ufw route delete allow in on wg0 out on eth0 PreDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE PreDown = ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
Allow forwarding IPv4 and IPv6 traffic that comes in on the wg0 VPN interface to the eth0 network interface on the server. And configures masquerading, and rewrites IPv4/IPv6 traffic that comes in on the wg0 VPN interface to make it appear like it originates directly from the WireGuard Server’s public IPv4/IPv6 address
Name of interface (eth0 for example), we can see by that commands.
# ip a # ip route list
2.3. Allow IP forwarding.
# sudo nano /etc/sysctl.conf
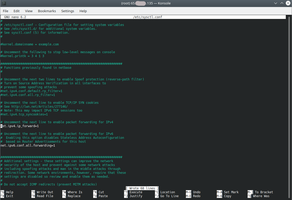
And than reload sysctl.
# sudo sysctl -p
2.4. Start WireGuard server.
At this point WireGuard server is fully workable and we can start it. Best way that UFW can disable at this point.
# sudo systemctl enable [email protected] # sudo systemctl start [email protected] # sudo systemctl status [email protected]
We can see this result.
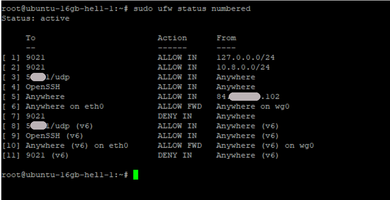
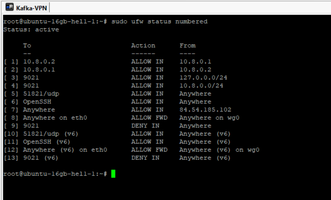
2.5. Setup UFW rules on server.
This is most important step because wrong rules can be block server for himself. Therefore I recommend as top rules number one is rule to allow admin to any access to server. This is rule number 3 on the screen above.
Common format of UFW is:
# sudo ufw deny/allow from xxx.xxx.xxx.xxx # sudo ufw deny/allow from xxx.xxx.xxx.xxx/yy # sudo ufw deny/allow in/out on eth0 from xxx.xxx.xxx.xxx # sudo ufw deny/allow “OpenSSH” # sudo ufw deny/allow from xxx.xxx.xxx.xxx/yy proto tcp/udp to any port 22 # sudo ufw deny/allow from xxx.xxx.xxx.xxx/yy to any port zzzz # sudo ufw allow 443 # sudo ufw allow proto tcp from any to any port 80,443
At any moment we can controlled opened port by
# sudo netstat -tulpn | grep LISTEN # sudo lsof -i -P -n | grep LISTEN
But main point is order of rules, because each rules close on top with less number override rules on bottom. Rules can not changed by place, only deleted and created again.
# sudo ufw status numbered # sudo ufw delete 6 # sudo ufw insert 1 allow from 10.8.0.0/24 to any port 9021 # sudo ufw insert 1 allow from 127.0.0.1/24 to any port 9021
Common command of manipulation UFW is
# sudo ufw enable/disable # sudo ufw status
Also we can take a list of application.
# sudo ufw app list
Pay attention how order of rules is important, for example if you try to add rules with open port 9021 automatically it start to position 6 and access to Confluent Control Center will impossible. Only manually ordered list allow insert this rules to position 1/2 and overload disable this port anywhere except VPN.
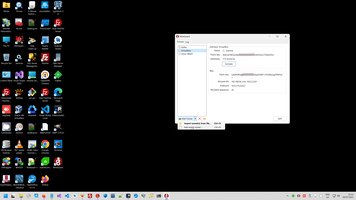
3. Install WireGuard client on Windows and Android phone.
Generate client public key.
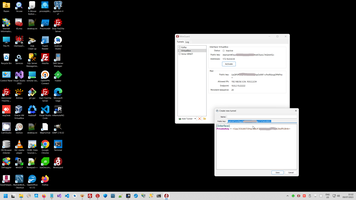
Add information about server as [peer].
The same operation we need to make in Android phone.

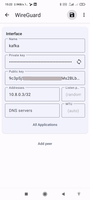
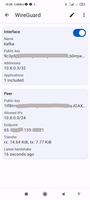
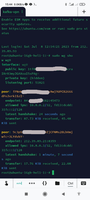
4. Add permission to connect VPN client to server.
This is last step of puzzle. Ipv6 is example.
# sudo wg set wg0 peer xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx allowed-ips yy.yy.yy.yy,fd11:1111:1111::1
After that client allow connection to server.
# sudo wg # watch wg
4. Final checking.
Final result can be the same. Globally Confluent Control Center closed from unauthorized access and opened for VPN users.
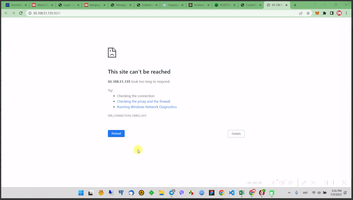
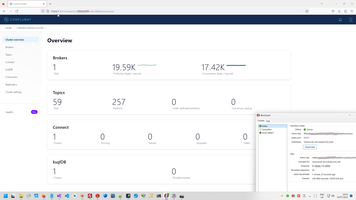
5. Working programmatically through VPN.
For this reason need to add two additional rules on top.
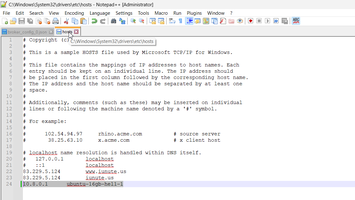
 )
)
| <SITEMAP> <MVC> <ASP> <NET> <DATA> <KIOSK> <FLEX> <SQL> <NOTES> <LINUX> <MONO> <FREEWARE> <DOCS> <ENG> <CHAT ME> <ABOUT ME> < THANKS ME> |